Release SABIO 5.28
Optimization of Inheriting Validities of Tree Nodes
With version SABIO 5.27, we have introduced the option to inherit validities that are initially set on a tree node to its subtree nodes and subcontent. With this release, changes to existing validities as well as deleting validities will also be inherited.
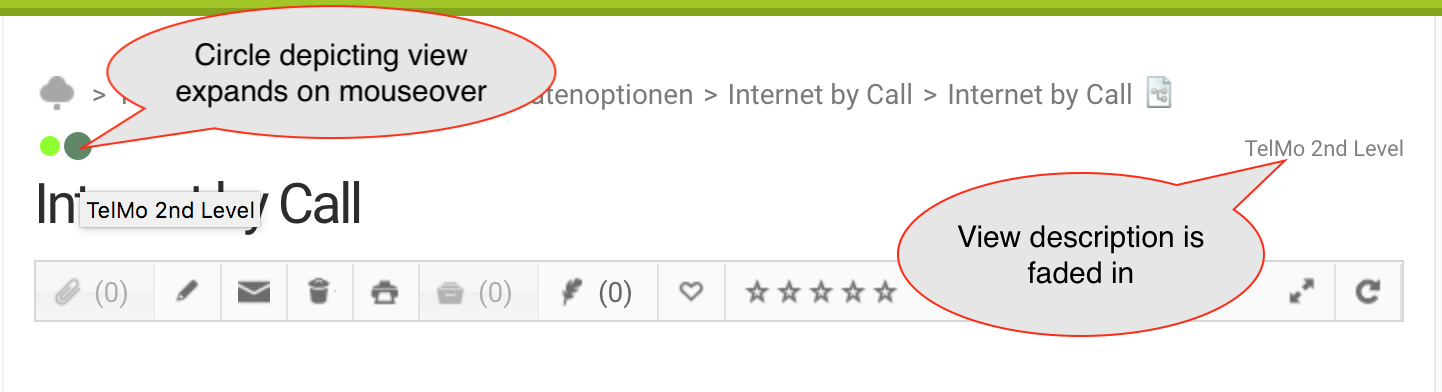
Optimized Display of Views in Detail View
In the detail view of knowledge content, the views assigned to the respective content are displayed between the path and the title of the content. This way, all views can be displayed, even if there are many views assigned to a content with a long path. If you hover over one of the colored circles depicting the views, it will expand and its name will be displayed.
Texts Are Deleted When Deleting Their Last Path
The behaviour when deleting texts has been optimized. You can remove texts from your SABIO system in two different ways - either by using the "Delete" icon in the toolbar in the detail view of a text, or by deleting the last path to the text.
The last path to the text itself cannot be deleted in edit mode. This can only be done via the tree by deleting the last tree node with the text.
Attention: When deleting a tree node, there is currently no validation whether it is the last path to a text.
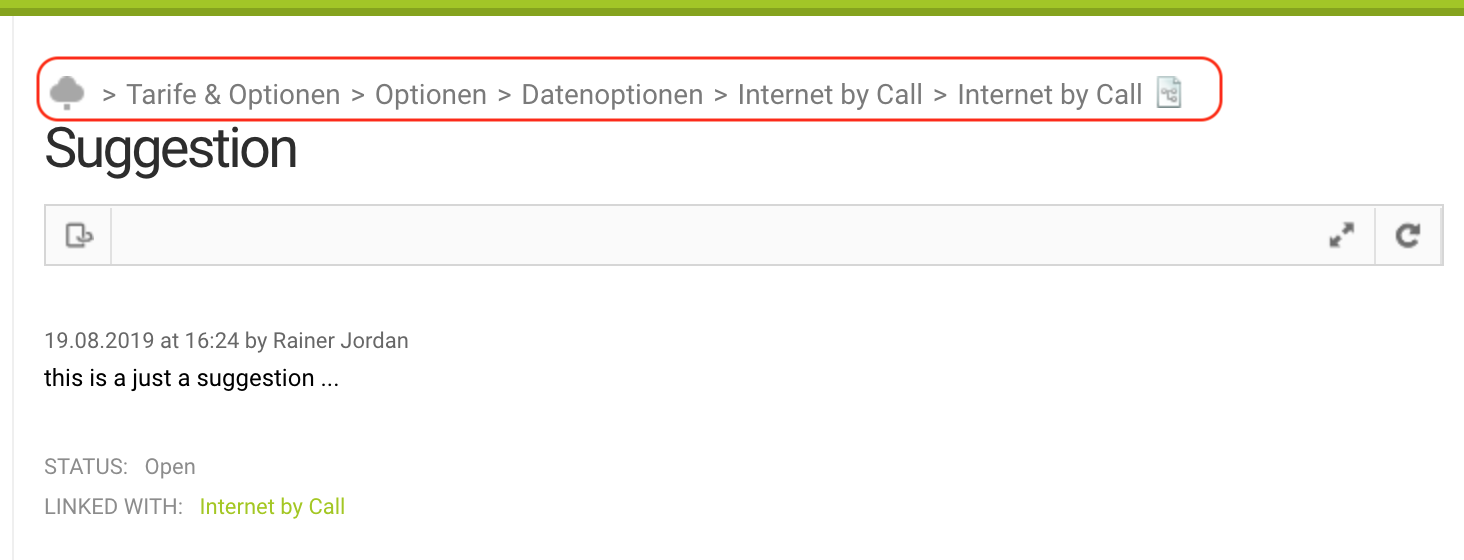
Path in the Detail View of Suggestions
The detail view of suggestions now also shows the path of the text for which the suggestion was created. If you click on a section of the path, the tree, in which the path to the clicked tree node is marked, opens as usual.
All Administrators May Edit Client Settings
All administrators with the permission "May edit system settings level1" also get the permission "May set realm client settings". This allows them to deactivate/activate the functions introduced in previous versions such as "Show attached documents in texts by default" or "Deleting texts and tree nodes requires an additional user confirmation" without having to contact SABIO Support.
The mentioned settings can be found as usual in the admin tab under “Settings”.
All Administrators May Administer Placeholders
All administrators with the permission "May edit system settings level1" also get the permissions to manage placeholders. These are:
- "May see placeholders"
- "May create placeholders"
- "May edit placeholders"
- "May delete placeholders"
- "May assign placeholders"
Improved Authentication Security - Migration Possible
With this version it is possible to switch the authentication for username/password to Keycloak. With this change you benefit from current security standards regarding authentication and storage of passwords.
Keycloak is an open source identity and access management solution that targets modern applications and services. This allows applications and services to be secured with little or no self-written code. [Source: https://www.keycloak.org/about.html]
Keycloak will be our standard interface for any kind of authentication in the future and already replaces our previous standard for SAML authentication.
If you would like to proactively change to the new Keycloak interface or receive more information, please contact us.
If you switch to Keycloak, all your existing users will be migrated to Keycloak so that you can log in with your usual access data after the migration. SABIO is responsible for all the costs involved in the change.
We will contact you in due course if you have not yet commissioned us to carry out the migration. By the end of 2019, we plan to have all our customers in our hosting migrated to authentication via Keycloak.
What does the change mean for you?
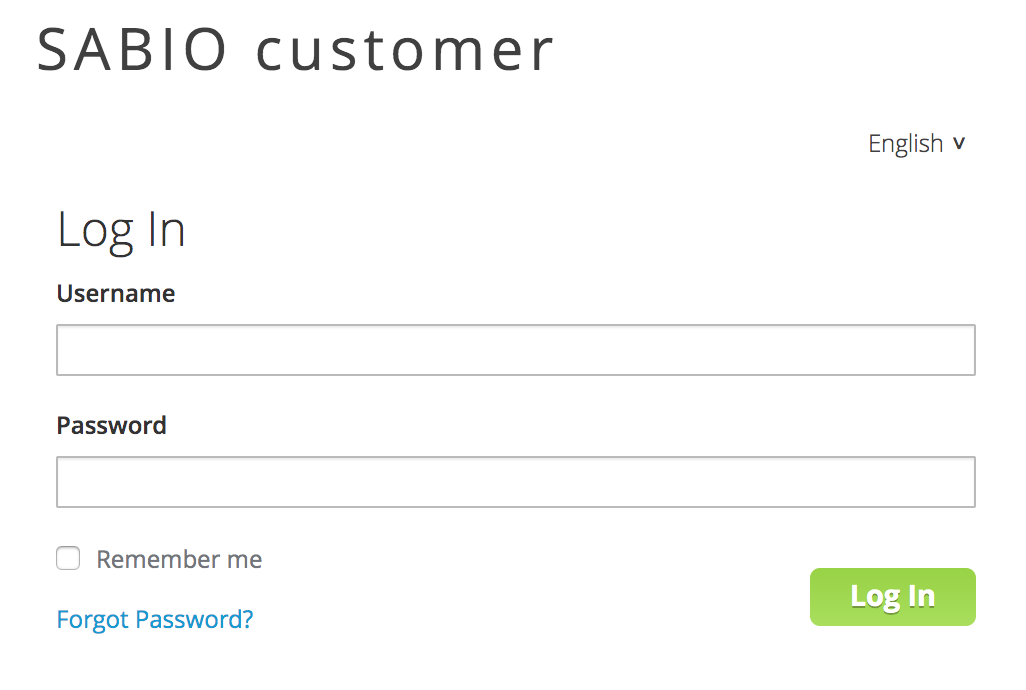
Login Mask
The most obvious change concerns the login mask.
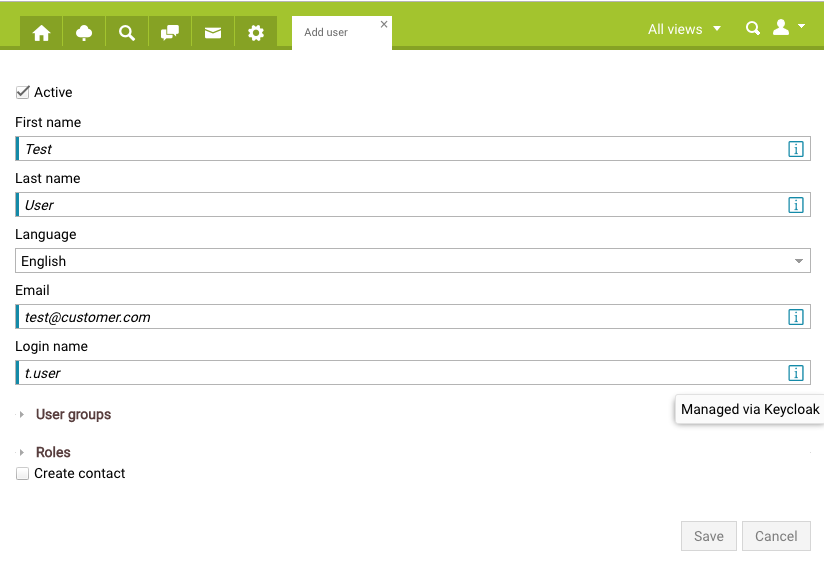
Adjustments in the user administration
-
The "Login Name" can no longer be changed. It can only be set when a user is created.
-
Passwords are only stored in Keycloak. They can no longer be set or changed via the SABIO user interface.
-
Users can change their passwords via "Forgot password".
-
-
When creating or changing a user in SABIO, the personal (first name, last name, e-mail address, language) and the user name are stored simultaneously in Keycloak. This is made visually clear in the respective masks (see screenshot below).
-
Deleting a user in SABIO deletes the user in Keycloak at the same time.
Password Security
Since passwords are stored only in Keycloak, the password security settings are also managed exclusively in Keycloak after the migration. This is currently only possible through our support. Please feel free to contact us, if you wish to make an adjustment to the settings.
The possible guidelines Keycloak offers for password security are described here: Password Policy Types
In addition, there is the possibility to make the (automatic) guessing of passwords more difficult. More information can be found here: Password guess: Brute force attacks
If these are activated, it is recommended to use the default values of Keycloak. These are also mentioned in the documentation.
Automatic reactivation of users
If a deactivated user logs in to SABIO, this user is automatically reactivated.
As soon as a user account is reactivated, it consumes a license again. All his settings and bookmarks are available to the user again.
Login name is stored in lower case
The "Login name" is stored in lower case only. Previously stored login names stay as they are now for the moment. Like before you can add a login name including upper case characters, but they will be converted automatically to lower case during saving process. If you open the user profile later on, you will get to see the lower case login name only.
Like before you can type for authentication the login name with upper case characters too. Nevertheless it will be compared with the lower case version. In the past and also in future it is not possible to add the same login name just with different writings in character case.
Authentication via OpenId Connect
All clients can authenticate themselves to SABIO via OpenId Connect. Authentication via OpenId Connect currently coexists with the previously known methods. These old methods (e.g. login via /authentication/credentials or via API key) will be completely replaced by the new method in the course of the coming year. We will inform you about the exact timing in due time.
What exactly has to be done for the changeover to OpenId Connect depends on the type of integration of your client. We have included the most common types in our API documentation. We will be happy to send them to you on request.
The prerequisite for OpenId Connect is the switch to Keycloak.